Apple attributes Endpoint Security (ES) events as originating from “platform binaries” or not using the JSON key is_platform_binary. So what does it mean to be a platform binary?
TLDR;
For the most part, Apple-developed applications downloadable from the App Store are signed by an authority that is not considered a platform binary. This leads to a red non-Apple executable designation for specific Apple executables in ESEV.
Executables signed as follows will appear as Apple executables:
Authority=Software Signing
Authority=Apple Code Signing Certification Authority
Executables signed with the following will appear with a non-Apple designation:
Authority=Apple Mac OS Application Signing
Authority=Apple Worldwide Developer Relations Certification Authority
Details
While exploring events we noticed that some executables we expected to be “Apple executables,” like Pages.app, were showing up with the red non-Apple executable marker. After a quick confirmation that the underlying JSON contained is_platform_binary=false, this meant it wasn’t a JSON parsing error. is_platform_binary is a boolean JSON key/value pair in every Endpoint Security event. ESEV uses this to tag events as originating from an Apple executable or not.
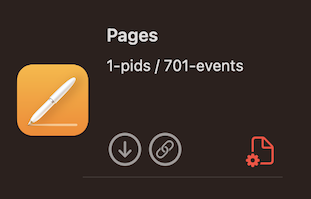
Our first thought was App Store. But Pages.app and Garageband.app were pre-installed on our machines. So although you can get them from the App Store, we did not.
We also noticed an inconsistency with executables within an application downloaded from the App Store – an example is shown below for Xcode.app. Some executables within the application are tagged non-Apple while others were not.
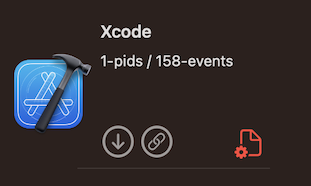
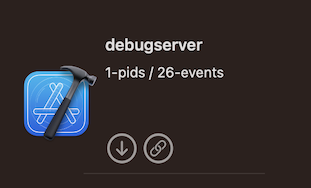
Ultimately, we correlated that all the executables showing up as non-Apple were downloadable from the App Store. This became obvious when noticing that Calendar.app shows up as an Apple executable but Pages.app does not. Pages.app is downloadable from the App Store even though it comes pre-installed, but Calendar.app is not downloadable from the App Store.
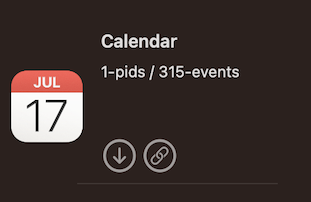
Using codesign, we dug a level deeper into the code signature differences between those two executables. For details on using codesign explore the post from Eclectic Light Company. codesign reveals that within the small sample set, two primary signing authorities lined up with executables being marked as a platform binary or not.
is_platform_binary=true
Authority=Software Signing
Authority=Apple Code Signing Certification Authority
is_platform_binary=false
Authority=Apple Mac OS Application Signing
Authority=Apple Worldwide Developer Relations Certification Authority
Caveat: There are numerous different Apple certificates and we did not perform an exhaustive exploration, nor did we see most in our sample set. The full list can be found here.
Another basic correlation from our limited exploration showed that applications in /System/Applications were tagged Apple and those in /Applications are not. Irrespective of if they are developed by Apple or not.
This is not definitive though, which is shown by Xcode.app which is downloadable from the App Store, contained in /Applications, but has several executables contained within that are signed as platform executables. Note, that the Finder UI merges the directories into a single view which it shows as /Applications. Therefore, to see the delineation it’s necessary to explore from the terminal.
For the most part, if it’s downloadable from the App Store it’s not considered a platform binary and will be marked as non-Apple in ESEV.