Heading back into early 2022 for this analysis post. [Objective-See’s post from January of 2022 details how SysJoker works. Let’s explore how this all looks and how to locate it using ESEV.
Objective-See maintains an awesome hosting of malware samples where we were easily able to download the SysJoker sample.
Extracting the zip file we find the malware types-config.ts.
The first order of business is to set up eslogger listening to the events we’re interested in.
nub@nubtop - % sudo eslogger btm_launch_item_add close create dup exec fork getextattr iokit_open mmap mprotect open readlink rename setextattr setmode uipc_connect write > malware.sysjoker.json
To follow along using ESEV at home, download the events.
Now, we needed to make the malware executable so we can infect the VM. We use UTM from the App Store and have been really happy with it so far. There is also a free version too.
nub@nubtop - % chmod +x types-config.ts
nub@nubtop - % ./types-config.ts
addToStatup
nub@nubtop - %
Executions and Persistence
Filter events using the left column exec. This will reduce the view from 17K+ events to just 21.
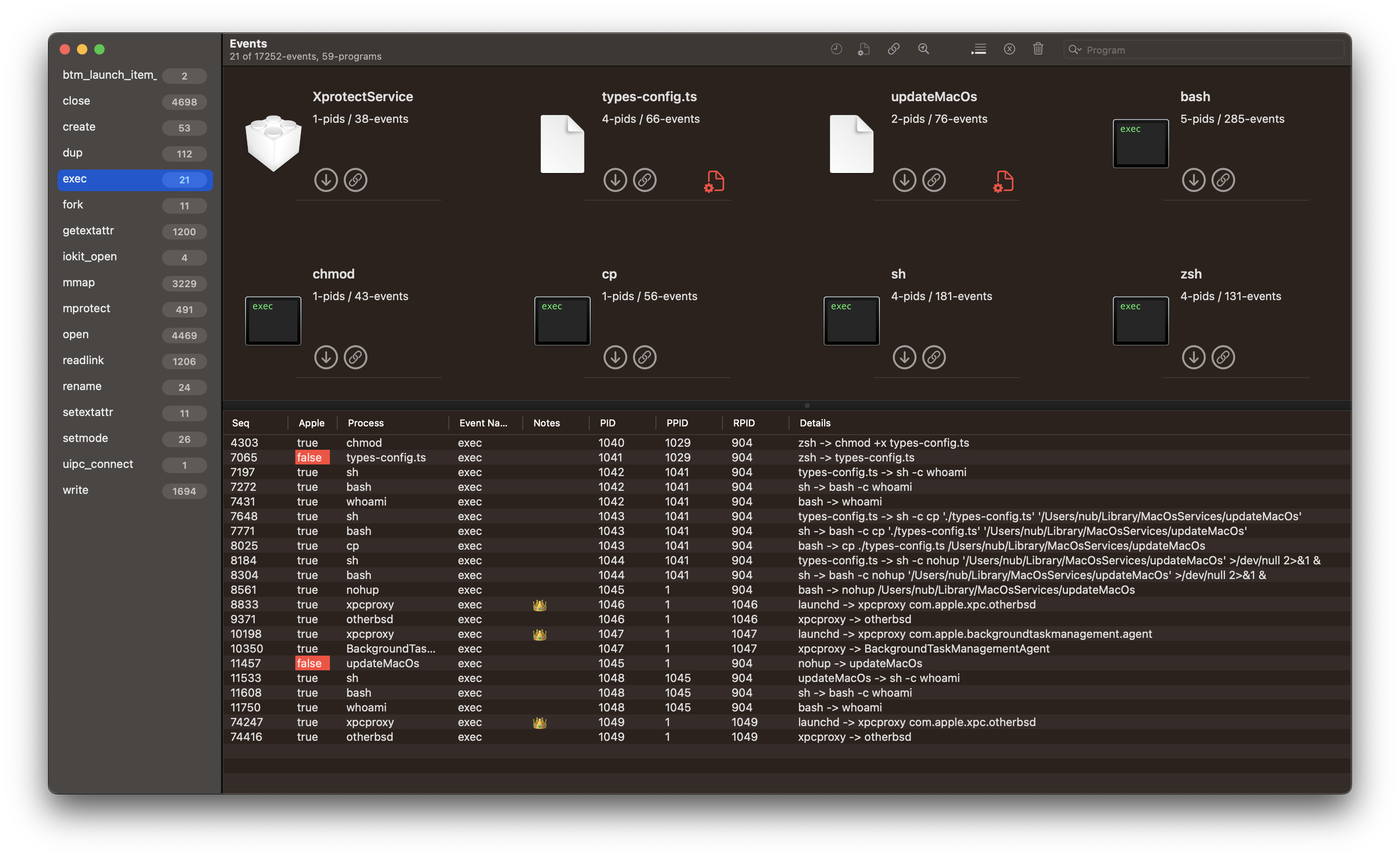
- seq #7197 the malware checks the user it’s executing as using
sh -c whoami. - seq #7648 the malware copies itself to a new location
sh -c cp ./types-config.ts /Users/nub/Library/MacOsServices/updateMacOs. - seq #8184 executes the newly created file using
nohupto enable the process to continue to run even if the user logs out.sh -c nohup /Users/nub/Library/MacOsServices/updateMacOs >/dev/null 2>&1 &
Exploring types-config.ts execution
Filter events using the upper-right column by selecting the program types-config.ts. This will reduce the view from 17K+ events to 66, focused on just the program. To reduce it even further select close, exec and fork` from the left column.
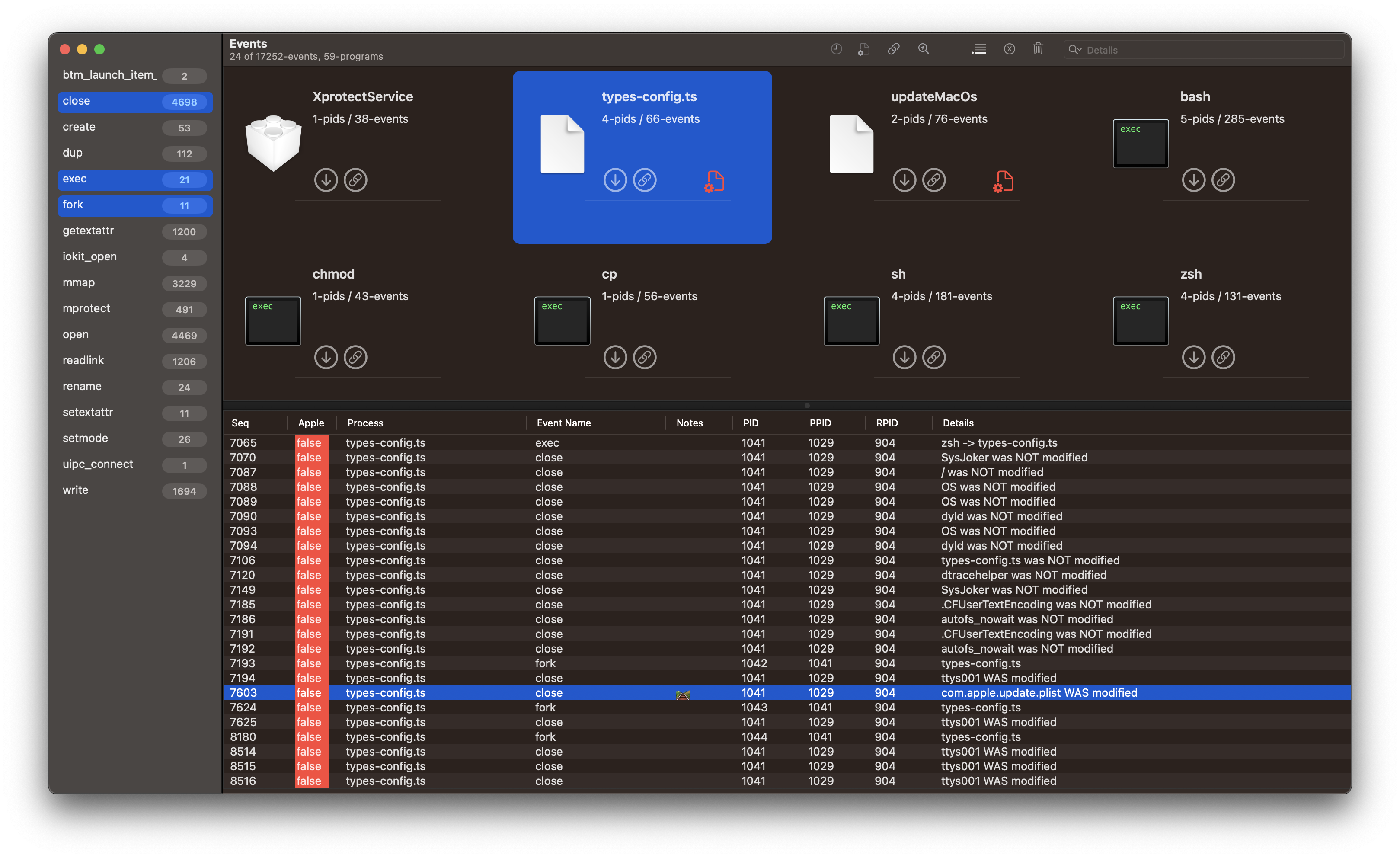
Startup
- seq #7603 shows a close event that notes the file was modified -
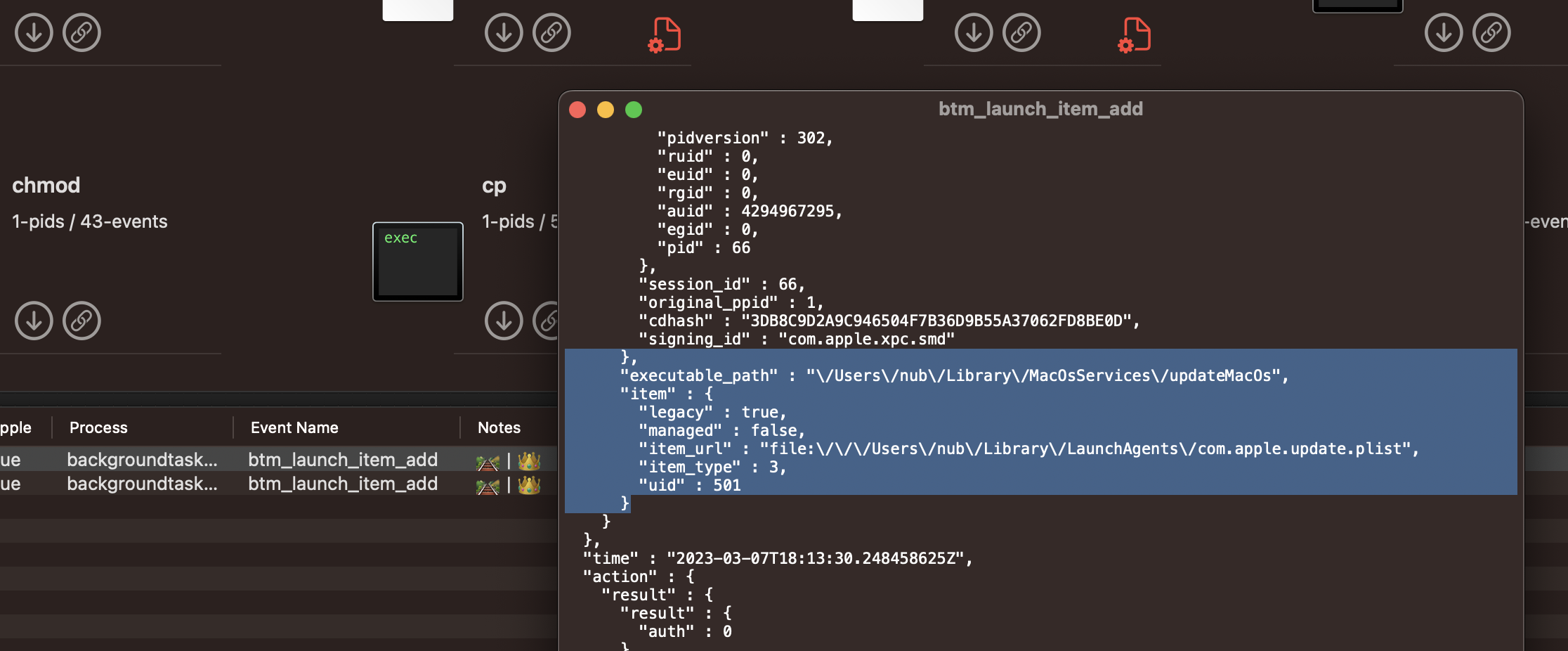
/Users/nub/Library/LaunchAgents/com.apple.update.plist. - seq #9811
updateMacOsandcom.apple.update.plistcan be seen as registered with SMAppService BackgroundTaskManagement (BTM).
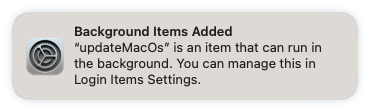
Here is a pop-up Users will see related to the change to BTM that has occurred
Exploring updateMacOs execution
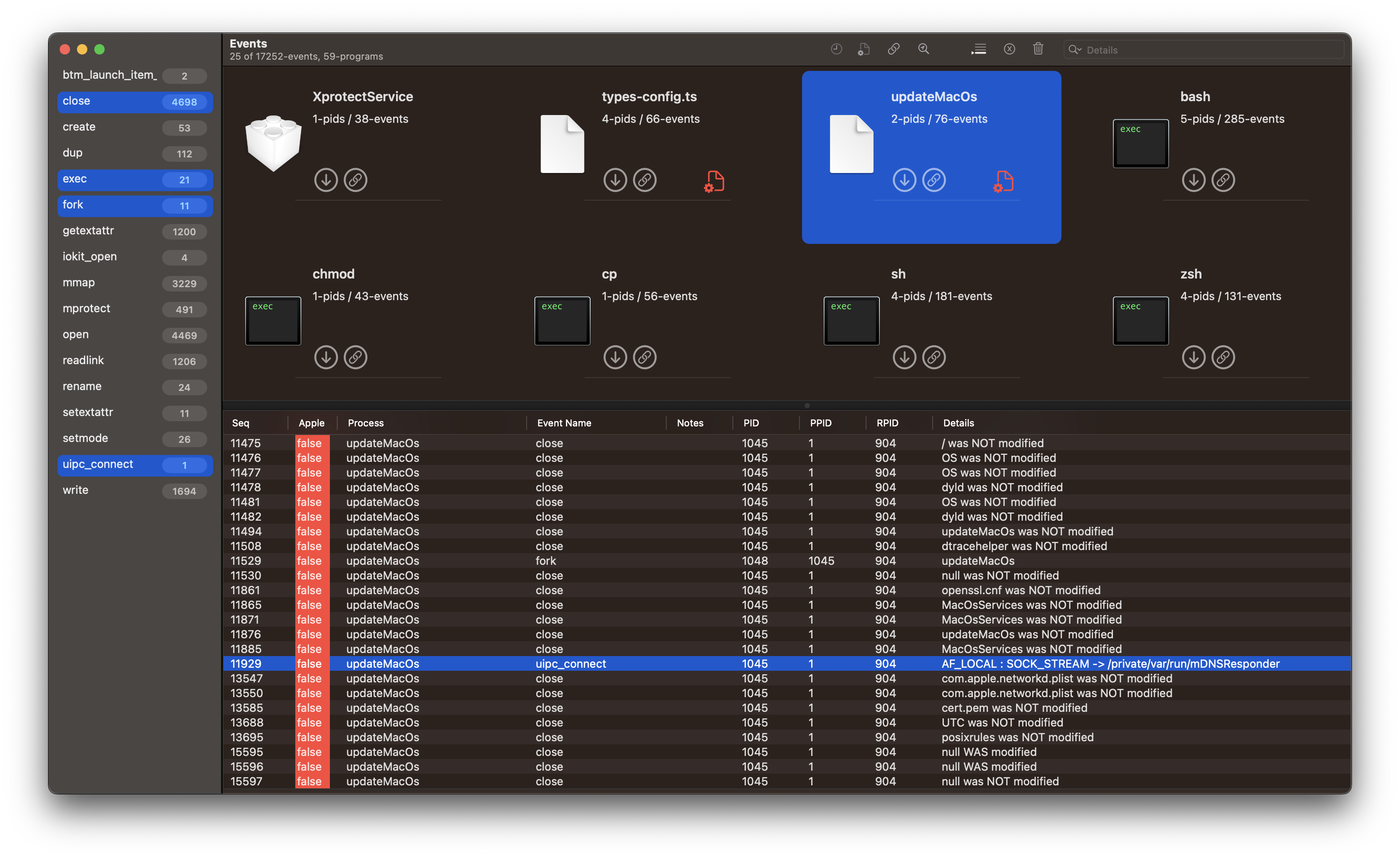
Networking - Comms
- seq #11860 shows
updateMacOsaccessingopenssl.cnfand seq #13584 shows it accessingcert.pem. Both of these indicate the malware may but using SSL network communication. - seq #11929
updateMacOsis creating a socket to mDNSResponder.
Those are the only indications of network activity that we get from eslogger.
As can be seen in Objective-See’s analysis network comms is occurring.
Using ESEV and eslogger we’re able to see:
- Persistence
- Relocating the malware
- Adding startup
- BTM
- Network (limited)
- SSL
- DNS