
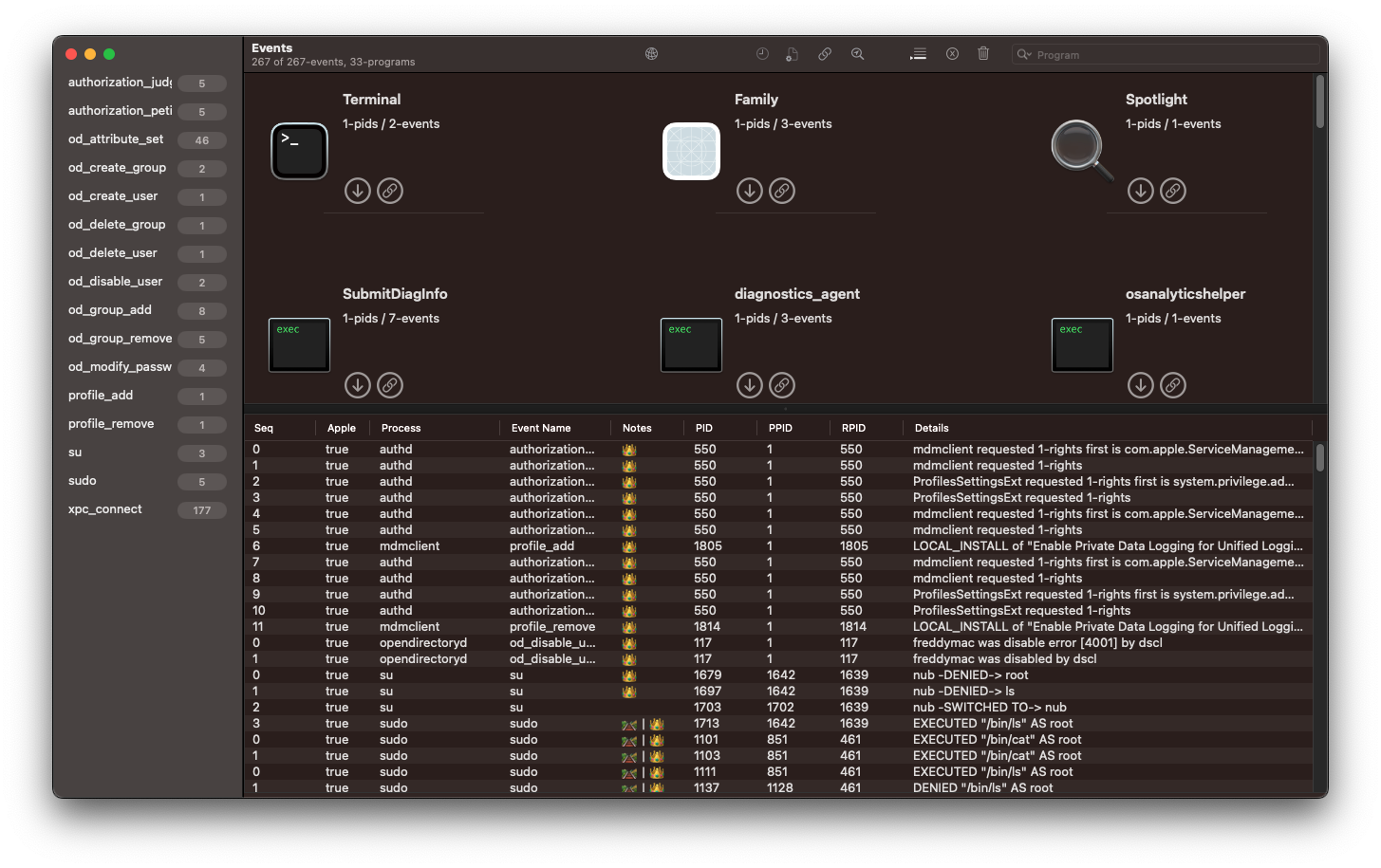
macOS 14.0 Sonoma beta brings the largest addition to Endpoint Security events since macOS Catalina (10.15.1) in 2019. Apple continues to improve the viability of a userland endpoint agent built atop macOS Endpoint Security. The newly added events allow monitoring of certain modifications to users, groups, MDM configuration profiles, XPC connections and privilege escalation.
20 new events in total, covering 5 distinct categories:
The new events help applications perform runtime malware analysis, detection, auditing and more. The newly added events are all notify-only, meaning detection only. Endpoint Security has two event types NOTIFY and AUTH. NOTIFY is for detection or auditing, informing that something occurred. AUTH is for prevention, asking if something should be allowed before it occurs.
The new events have been added to the latest release of ESEV, downloadable now!
Switching Identities (aka Elevating Privileges)
The su command, switch user or substitute, starts a new interactive shell as a different user. This is commonly used by a system administrator to complete a set of actions that require more privileges than the current user maintains. su allows them to temporarily switch to another (more privileged) user and execute commands.
In this event, Endpoint Security details from (sallymay:502) and to (nub:501) identities, showing who elevated to what privileges. Also included are the shell, the environment variables and the arguments used during the elevation.
"su": {
"from_uid": 502,
"failure_message": null,
"env": [
"USER=nub",
"HOME=/Users/nub",
"SHELL=/bin/zsh",
"PATH=/bin:/usr/bin",
"TERM=xterm-256color"
],
"argv": [
"-zsh"
],
"argc": 1,
"to_username": "nub",
"to_uid": 501,
"success": true,
"shell": "/bin/zsh",
"from_username": "sallymay",
"env_count": 5
}
sudo like su is also used by system administrators to elevate privileges. The difference is sudo executes a single command whereas su creates an interactive shell.
The sudo event contains limited details. Simply the command, from identity, and to identity. A detail to highlight about the sudo event is that it does not provide the full command executed, only the program name (argv[0]). It does not provide the arguments given to the program. In the example below we’re executing cat /etc/password but Endpoint Security only shows /bin/cat. If desired, monitor exec events along with sudo events. Then, temporally correlate the related exec event to see the full command with arguments.
"sudo": {
"from_uid": 501,
"success": true,
"command": "/bin/cat",
"to_uid": 0,
"reject_info": null,
"from_username": "nub",
"to_username": "root"
}
When sudo does not succeed, Endpoint Security provides details in reject_info as to why and what plugin denied the action.
nub@nubtop ~ % sudo ls /tmp
Password:
Sorry, try again.
Password:
Sorry, try again.
Password:
sudo: 3 incorrect password attempts
nub@nubtop ~ %
Here we can see the wrong password was entered.
"sudo" : {
"to_uid" : 0,
"from_username" : "nub",
"to_username" : "root",
"success" : false,
"command" : "\/bin\/ls",
"reject_info" : {
"plugin_type" : 1,
"failure_message" : "authentication failure",
"plugin_name" : "sudoers_policy"
},
"from_uid" : 501
}
Configuration Profiles
Configuration Profiles are most notably used for MDM enforcement of system configuration, but they can also be used locally for running beta software, viewing “encrypted” system logs, etc. Tracking configuration profiles is will help system administrators to understand what is and is not properly configured on a system.
After adding a new configuration profile, Endpoint Security provides details about the process (instigator) that added the profile and metadata about the configuration profile itself like name and UUID. We’re also told whether the profile was added using MDM or locally installed, install_source. Unfortunately, no extra install details are available such as the MDM server or file path. Adding and removing profile events both provide the same details. Below is the Endpoint Security message from loading a Configuration Profile downloaded from Kandji.
"profile_add" : {
<...snip...>,
"profile": {
"organization": "",
"display_name": "Enable Private Data Logging for Unified Logging",
"scope": "system",
"identifier": "25B5F357-988A-4BE8-BF2D-684287B1FBA2",
"install_source": 1,
"uuid": "298372EA-B0B7-4C11-94D7-DA99220A6F07"
}
}
Open Directory Admin
Most of the new events Apple added are in Open Directory. They monitor the configuration of users, groups, attributes, and passwords. There are many uses for tracking when users are created or deleted, users are added or removed from groups, when groups are created or deleted, etc. Note, these events only trigger when the modifications are with Open Directory.
We received ES notifications using both System Settings and dscl to modify users and groups.
| Create User | Add to Group |
|---|---|
 |
 |
nub@nubtop ~ % sudo dscl . -create /Users/sallymay
Password:
nub@nubtop ~ % sudo dscl . -create /Users/sallymay RealName "Sally May"
nub@nubtop ~ % sudo dscl . -create /Users/sallymay UserShell /bin/zsh
nub@nubtop ~ % sudo dscl . -passwd /Users/sallymay <password>
nub@nubtop ~ % sudo dscl . -append /Groups/MyNewGroup GroupMembership sallymay
nub@nubtop ~ % sudo dscl . -delete /Users/sallymay
Below, we can see the creation of a new user sallymay. The user is added to the local database. The process (instigator) that requested the action was snipped from the JSON below for brevity but in this case was “path”: “/usr/libexec/opendirectoryd”.
"od_create_user": {
"db_path": "/var/db/dslocal/nodes/Default",
"error_code": 0,
"user_name": "sallymay",
"node_name": "/Local/Default",
<...snip...>
}
When creating a new user or group, od_attribute_set events show the set of LDAP attributes that were configured during user creation. There are likely 100s of potential attributes ranging from email address to phone number to _writers_AvatarRepresentation. Listing all the attributes is beyond the scope of this article.
Here we can see the user sallymay being added to the group TheNewGroup.
"od_group_add": {
"group_name": "TheNewGroup",
"error_code": 0,
"member": {
"member_type": 0,
"member_value": "sallymay"
},
<...snip...>
}
macOS Endpoint Security also shows user accounts being enabled and disabled. Remember, this is only within the context of Open Directory. So disabling a user with pwpolicy, sysadminctl, or chsh will not be detected.
However, it does detect changes through Directory Utility, dscl and many made in System Settings. For example:
nub@nubtop ~ % dscl . -append /Users/freddymac AuthenticationAuthority ";DisabledUser;"
generates
"od_disable_user": {
"node_name": "/Local/Default",
"user_name": "freddymac",
"error_code": 0,
"db_path": "/var/db/dslocal/nodes/Default",
"instigator": {
"executable": {
"path": "/usr/bin/dscl",
<...snip...>
}
Authorization Rights
The new authorization events track requests and responses for Authorization Rights. For details on Authorization Rights in macOS, we recommend starting with the post by TheEvilBit. Below is an event where a process was granted the system.privilege.admin right. These events contain the process that created the request (petitioner) as well as the process that submitted the request (instigator). They may be the same process, but not always depending on how the software was architected.
"authorization_judgement" : {
"result_count" : 1,
"return_code" : 0,
"results" : [
{
"rule_class" : 0,
"right_name" : "system.privilege.admin",
"granted" : true
}
],
"instigator": <...snip...>,
"petitioner": <...snip...>
}
XPC
Track XPC connections to named services. This event generates a LOT of events and should be used accordingly.
"xpc_connect" : {
"service_name" : "com.apple.tccd.system",
"service_domain_type" : 1
}
List of new macOS Sonoma ES Events
authorization_judgement
authorization_petition
od_attribute_set
od_attribute_value_add
od_attribute_value_remove
od_create_group
od_create_user
od_delete_group
od_delete_user
od_disable_user
od_enable_user
od_group_add
od_group_remove
od_group_set
od_modify_password
profile_add
profile_remove
su
sudo
xpc_connect
Links
https://developer.apple.com/documentation/endpointsecurity/endpointsecurity_structures?changes=lat_3 https://developer.apple.com/documentation/endpointsecurity/3228936-es_events_t https://support.apple.com/guide/security/configuration-profile-enforcement-secf6fb9f053/web https://developer.apple.com/business/documentation/Configuration-Profile-Reference.pdf https://theevilbit.github.io/posts/macos_authorization/ https://developer.apple.com/library/archive/documentation/Security/Conceptual/authorization_concepts/02authconcepts/authconcepts.html